- Vulnerable U
- Posts
- 🎓️ Vulnerable U | #088
🎓️ Vulnerable U | #088
Microsoft threat actor reports, Sophos hack back against Chinese APT, Disney insider threat, some supply chain bugs in Fortune 500 companies, and more!
Read Time: 9 minutes

Howdy friends!
Happy Halloween! My costume is SUPER scary this year. Hope you all can sleep at night.

Been really feeling the mental toll of the U.S. Election right now so I wrote about it.
Yesterday, a family member sent me another forwarded message about election fraud being coordinated through compromised voting machines. As someone who works in cybersecurity, I knew immediately it wasn't true - the technical claims were nonsensical. But how do you tell your own family they’ve been deceived without damaging your relationship?
There is only so many times you can point out a website or Facebook page is satirical, misinformation, AI generated, or just otherwise fake, before your relationship just really degrades.
We're living through a unique moment in history where those of us in cybersecurity and tech have a front-row seat to how misinformation campaigns actually work. We see the infrastructure, recognize the patterns, and understand the mechanisms of viral distribution. But that knowledge comes with a heavy psychological burden - especially during election season.
It's one thing to deal with phishing attempts and security breaches at work. It's another entirely when you watch people you care about fall for sophisticated influence campaigns in real-time. The mental toll of living in what feels like a different reality from your friends and family is rarely discussed in our industry, but it's becoming a critical mental health issue.
Here's what makes this particularly challenging for those of us in tech:
ICYMI
🖊️ Something I wrote: Alert Fatigue can get to all of us. Did you see my post last week about strategies to combat it?
🎧️ Something I heard: Was talking to someone who is watching Rings of Power but hasn’t read the Lord of the Rings books and had to explain Tom Bombadil. Found a video to help.
🎤 Something I said: Talked to the legend Paul Asadoorian on his podcast last week.
🔖 Something I read: Since I finished the Stormlight Archive, I went ahead and picked up the rest of the Cosmere Universe books I hadn’t read yet. Got some funny looks at the bookstore.

📣 Sponsor
Ultimate Guide: Extend Wiz to Your Developers
With the speed at which companies are developing cloud-native applications, as well as recent trends in DevOps & GenAI, “shifting left” and extending your cloud security architecture into your developer environments is a critical component of a mature cloud security program.
But where do you start, and how do you build such a program?
Dive into this comprehensive guide to securing your code environments and enabling your developers to safely build applications at a transformative speed and scale.
Vulnerable News
Sophos X-Ops unveils five-year investigation tracking China-based groups targeting perimeter devices
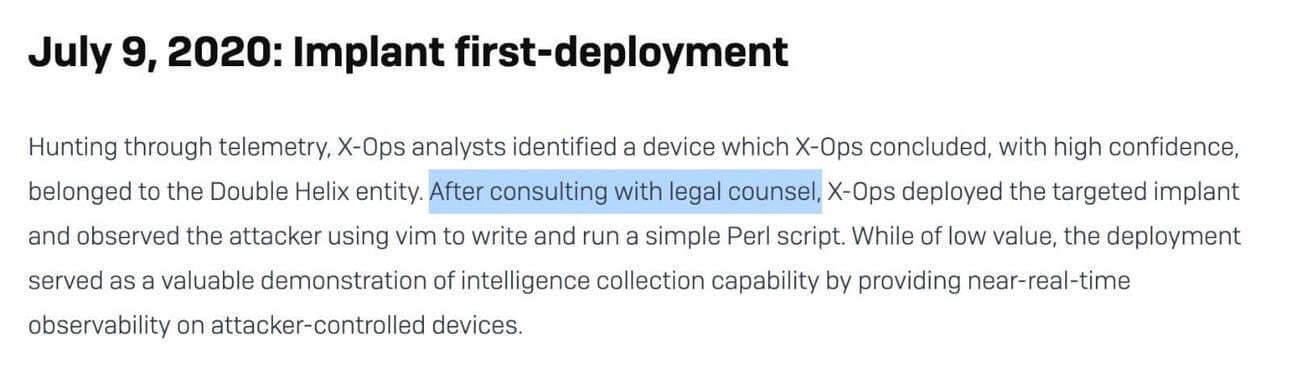
Wow, Sophos just dropped a massive report detailing their 5-year battle with Chinese APT groups targeting network devices. Not often we get to read about the results of a “hack back” campaign. Thanks to the lawyers who let this happen, we get a lot of great data!
The timeline starts with a 2018 attack on their Cyberoam offices in India and follows through multiple zero-days and sophisticated campaigns. The attackers evolved from mass exploitation to targeted attacks against government, military, and critical infrastructure, primarily in Asia.
The attackers kept submitting their zero-days through bug bounty programs right before exploiting them in the wild (!!!), and they developed some pretty sophisticated rootkits, including one that could survive firmware updates. They also caught the attackers testing their exploits from research labs in Chengdu.
Check out the full report that details this APT’s behavior change over the 5 years Sophos monitored them via their implant without them knowing. (read more)

Midnight Blizzard (Russia's SVR crew) is back with a fresh spear-phishing campaign that's hitting over 100 orgs as we speak. They're using signed RDP config files as the payload this time - a first for them. Once opened, these files phone home to their C2 and start dumping all sorts of juicy system info like disk contents, clipboard data, and connected devices.
The lures are pretty slick - they're crafting emails about Azure, Zero Trust, and AWS to hook IT folks, and they're sending them from previously compromised accounts for that extra legitimacy boost. Microsoft caught wind of this on Oct 22nd and says it's still going strong, mainly targeting government agencies and educational institutions across the UK, Europe, Australia, and Japan. Classic SVR targeting, new tricks. (read more)
This is just messed up. (read more)
Microsoft just dropped some intel on a Chinese threat actor (Storm-0940) that's been stealing credentials through a clever password spray setup. They're using what Microsoft calls "CovertNetwork-1658" - basically a network of hacked TP-Link routers that act as their proxy army. They only try one password per account per day to stay under the radar, and they're quick to use any credentials they steal.
The good news is that after some security firms exposed this network over the summer, their infrastructure took a nosedive - dropping from about 8,000 compromised devices to way fewer. But Microsoft thinks they're probably just retooling with new infrastructure rather than calling it quits. (read more)
Well we knew this was a big one but we have numbers now. UnitedHealth finally confirmed what many suspected - the Change Healthcare ransomware attack from February impacted 100 million people's healthcare data. That's nearly a third of the U.S. population and the largest healthcare breach ever recorded. For context, the next biggest breach only hit 14.76 million people.
The initial compromise was pretty basic - attackers used stolen creds to access a Citrix portal that didn't have MFA enabled (ouch). They later paid a $22M ransom but the damage was done. The breach caused massive disruptions across hospitals and pharmacies nationwide, really highlighting how interconnected (and vulnerable) our healthcare infrastructure is.
Change Healthcare is one of those companies you’ve never heard of unless you’re in that field, and then you find out nearly all our healthcare billing relies on them. (read more)

You know its bad when the law enforcement operation has a name, brand, website, and what seems like a marketing budget. - Operation Magnus just took down RedLine and Meta infostealers. This was a sizable bust, seizing domains, servers, and even some arrests including RedLine dev Maxim Rudometov. The operation involved six countries working together and managed to get their hands on the full infrastructure.
The scale here is pretty wild - they found over 1,200 servers across dozens of countries and recovered millions of stolen credentials. Law enforcement also snagged the client database, so expect more shoes to drop as they dig through that treasure trove of who's been buying these malware-as-a-service packages. (read more)

A security team was testing their new tool, Depi, when they stumbled onto something juicy in HashiCorp's Consul codebase - some wildcard dependencies that could be hijacked. While they initially thought it only affected pnpm users, they claimed the packages anyway to demo the issue. Plot twist: they got a ping from inside a Fortune 500 company's network, showing the vulnerability was way more widespread than expected. Turns out npm was vulnerable too.
The impact was pretty significant - they scored a $17k bounty from the Fortune 500 company and got HashiCorp to patch Consul versions 1.12.0 through 1.19.0. The fix was simple but effective: switching from wildcard dependencies (*) to explicit file references. Classic case of a small config oversight leading to a potentially nasty supply chain attack. Props to both companies for handling the disclosure like pros. (read more)
Looks like Russia finally wrapped up that REvil case from 2022. Four members got sentenced to 4.5-6 years in prison, though they've already served some time since their arrest. They're not being charged for any of the big ransomware attacks we know about - just some card fraud and malware distribution charges.
What's really eyebrow-raising here is that Russia actually followed through with prison sentences instead of recruiting these hackers for their cyber ops against Ukraine or the West. For comparison, a Ukrainian REvil affiliate got slapped with 13 years in a U.S. prison earlier this year. Makes you wonder if this is Russia trying to save face internationally or if there's more to the story we're not seeing. (read more)
Well this is interesting - looks like North Korea's Andariel group is branching out into the ransomware-as-a-service game. Unit 42 caught them working with the Play ransomware crew in September, marking their first collab with an underground ransomware network. They got initial access in May through a compromised account, deployed their usual toys (DTrack malware, Impacket), then handed the keys over to Play for the ransomware finale.
The spicy part is we don't know exactly how deep this partnership goes. Could be Andariel just selling access as an IAB, or maybe they're a full-on Play affiliate (though Play claims they don't do RaaS). Either way, seeing NK state actors getting cozy with criminal ransomware groups is a concerning evolution of their usual espionage and custom ransomware ops. Looks like they're diversifying their portfolio! (read more)
We've got a massive e-commerce scam that's been flying under the radar since 2019. The "Phish n' Ships" campaign has compromised over a thousand legit online stores, injecting fake listings for hard-to-find items. When shoppers bite, they're redirected through a maze of fake stores that steal their cash and card details without ever shipping anything.
HUMAN's Satori team finally caught up with these folks and managed to disrupt their operation by getting Google to nuke the malicious listings and shutting down their payment processing. But you know how this goes - they'll probably be back with a new scheme soon enough. Bunch of damage already though, tens of millions in losses from hundreds of thousands of victims over five years. Not a bad haul for some crafty PHP scripts and SEO tricks. (read more)

Some good research about Chenlun/Sinkinto01 and some of their fancy new tricks. They've graduated from just USPS scams to Amazon account warnings, and they're getting craftier with their domain game. Instead of using obvious phishy domains, they're now running a domain generation algorithm and using short-lived subdomains on older apex domains to stay under the radar.
One part I honed in on was how they've adapted their infrastructure after getting heat - switching up their registrars from Dominet to NameSilo and moving from Alibaba Cloud to DNSOwl. They're also using redirect domains as an extra hop before collecting personal info. Props to DomainTools for tracking these evolution in tactics, though it's a bit concerning how sophisticated these SMS phishing campaigns are getting. (read more)
Delta just slapped CrowdStrike with a $500M lawsuit over that nasty outage from July when a bad Falcon Sensor update caused thousands of systems to blue screen. Delta says they had to cancel 7,000 flights and mess up travel plans for 1.3M customers, which is... not great.
CrowdStrike's not taking this lying down though. They're basically saying "hold up, this is on Delta's ancient IT infrastructure" and that they shouldn't be on the hook for more than $10M. Plus they're throwing shade at Delta for being slower to recover than other airlines that got hit with the same issue. Pete Buttigieg is apparently curious about that too - the DOT is poking around to figure out why Delta had such a harder time bouncing back. You know the real winners here though, right? Billable hour lawyers! (read more)
I spend a lot of my time worrying about time to find and time to fix vulnerabilities. Well this is one of those that would blow the metrics up a bit. qBittorrent just patched a 14-year-old security flaw that's been sitting there since 2010.
They weren't validating SSL certificates at all - just accepting whatever came their way. This meant anyone doing man-in-the-middle shenanigans could potentially slip in malicious code through update checks, RSS feeds, or even that Python installer prompt Windows users sometimes get.
Sharp Security found this one and demonstrated it by popping calc.exe (the classic security researcher move). The fix finally landed in version 5.0.1. What's interesting is the qBittorrent team quietly fixed this without a CVE or much fanfare. (read more)
Miscellaneous mattjay
How'd I do this edition?It's hard doing this in a vacuum. Screaming into a void. Feedback is incredibly valuable to make sure I'm making a newsletter you love getting every week. |
Parting Thoughts:
Community was foundational in launching and propelling my career. Community is the only reason I can stand being in Texas during the summer months. Community is the point. Today, I invite you to embrace discomfort on the road to a more vulnerable you.
Stay safe, Matt Johansen
@mattjay

